Se connecter à un serveur vpn
Retour d'expérience
Système et matériels / Réseau Internet Wi-Fi
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
Voilà, j’ai installé un serveur openvpn sur mon raspberry pi/raspbian. Cela n’a pas été aisé, mais le service fonctionne correctement, notamment depuis mon téléphone mobile.
Pour configurer le client Mageia, c’est loin d’être simple, même si je suis parvenu à me connecter à ce service. Toutefois, je ne suis pas satisfait dans l’état de la situation.
Pour la partir serveur openvpn, j’ai suivi le tuto suivant en y apportant quelques modifications :
- La connexion se fait non pas en tcp mais en udp. C’est pourquoi dans le fichier de configuration du serveur.conf, j’ai « proto udp # protocole à utiliser : tcp ou udp »
- J’ai installé le paquet iptables-persistent pour conserver les règles iptables au reboot, plutôt que de créer un script pour cela.
Code BASH :
echo 1 > /proc/sys/net/ipv4/ip_forward iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE iptables-save > /etc/iptables/rules.v4 systemctl enable netfilter-persistent
Voici le fichier configuration du serveur :
Code TEXT :
local 192.168.1.2 # adresse IP locale de votre serveur dev tun # type de VPN, tun (tunnel IP) ou tap (tunnel Ethernet/bridge) proto udp # protocole à utiliser : tcp ou udp, généralement udp port 1194 # le port par défaut pour OpenVPN, à ajuster au besoin ca /etc/openvpn/easy-rsa/keys/ca.crt # clé publique de l’autorité de certification cert /etc/openvpn/easy-rsa/keys/server.crt # Clé publique du serveur key /etc/openvpn/easy-rsa/keys/server.key # Clé privée du serveur von dh /etc/openvpn/easy-rsa/keys/dh2048.pem # si vous êtes restés sur du 2024 bits server 10.8.0.0 255.255.255.0 #le réseau au sein duquel vous allez attribuer des IP. Les clients auront une ip en 10.8.0x push "redirect-gateway def1" push "dhcp-option DNS 10.8.0.1" # votre serveur DNS primaire (votre routeur, souvent) # vous pouvez aussi utiliser le DNS Google 8.8.8.8 ou OpenDNS 208.67.222.222 # pour le reste, a priori pas de raisons d'y toucher à moins de savoir ce que vous faites ! client-to-client duplicate-cn keepalive 10 120 tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0 cipher AES-128-CBC comp-lzo user nobody group nogroup persist-key persist-tun status /var/log/openvpn-status.log 20 log /var/log/openvpn.log verb 3
Vous noterez que pour le dhcp-options, l’adresse ip est celle de mon serveur raspberry (10.8.0.1) qui fait office de serveur vpn et de serveur dns. J’ai en effet un service unbound pour le dns et un serveur dhcp. Pourquoi cela, parce que j’ai une livebox qui ne sait pas gérer correctement le loopback. En effet, j’ai un nom de domaine gandi. A l’extérieur, l’ip est celle de ma livebox (IP WAN) réactualisée via l'API Gandyn depuis le raspberry via l'outil Gandyn. En revanche, pour indiquer l’ip du serveur depuis le réseau local aux client, la livebox n’est pas capable de me renvoyer l’ip (LAN) du pi. Le service Unbound me permet de contourner le problème en précisant l'IP du pi2.
Pour openvpn, lors de mon installation, j’ai généré les certificats et clés clients. J’ai créé un fichier client.ovpn qui comprend :
- Le fichier de configuration du client
- La clé privée client.3des.key
- La clé publique client.crt
- La clé publique de l’autorité de certification : ca.crt
- La clé tls-auth ta.key
Le fichier de conf du client comporte :
Code TEXT :
client dev tun proto udp # Protocol udp remote mon_domaine.fr 1194 # on peut mettre l'ip du serveur vpn, ou le nom de domaine. On retrouve le port 1194 resolv-retry infinite nobind persist-key persist-tun mute-replay-warnings ns-cert-type server key-direction 1 cipher AES-128-CBC comp-lzo verb 1 mute 20
Le fichier client.ovpn est généré via le script MakeOpenVPN.sh. C'est le fichier qui sera employé notamment par le client android openvpn.
....La suite dans le post ci dessous
Édité par vouf Le 19/12/2015 à 13h35
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
Passons maintenant à la configuration du client Mageia
J'ai donc installé openvpn sur une mageia 5 64 bits. Dans un premier, je suis passé par la méthode hardcore qui finalement me semble actuellement la plus simple.
Sur ma machine de test je suis en wifi. Je me connecte root et lance la commande openvpn avec le fichier de configuration en paramètre.
Code BASH :
[root@localhost ~]# openvpn --config /home/vouf/openvpn/client.ovpn Sat Dec 19 09:47:50 2015 OpenVPN 2.3.6 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Dec 27 2014 Sat Dec 19 09:47:50 2015 library versions: OpenSSL 1.0.2e 3 Dec 2015, LZO 2.09 Enter Private Key Password: ********************* Sat Dec 19 09:48:03 2015 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Sat Dec 19 09:48:03 2015 Control Channel Authentication: tls-auth using INLINE static key file Sat Dec 19 09:48:03 2015 UDPv4 link local: [undef] Sat Dec 19 09:48:03 2015 UDPv4 link remote: [AF_INET]192.168.1.2:1194 Sat Dec 19 09:48:03 2015 [server] Peer Connection Initiated with [AF_INET]192.168.1.2:1194 Sat Dec 19 09:48:06 2015 TUN/TAP device tun0 opened Sat Dec 19 09:48:06 2015 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0 Sat Dec 19 09:48:06 2015 /usr/sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500 Sat Dec 19 09:48:06 2015 Initialization Sequence Completed
Comme vous pouvez le constater, la connexion au serveur vpn fonctionne. Il me demande le mot de passe configuré pour le client lors de la création de ses certificats. L'ip du client est 10.8.0.6, une interface "virtuelle" Tun a été créé.
Code BASH :
[root@localhost ~]# ifconfig -a enp9s0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500 ether 00:24:54:6c:2f:da txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 device interrupt 18 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 0 (Boucle locale) RX packets 428 bytes 34388 (33.5 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 428 bytes 34388 (33.5 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500 inet 10.8.0.6 netmask 255.255.255.255 destination 10.8.0.5 unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 wlp5s0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.1.13 netmask 255.255.255.0 broadcast 192.168.1.155 inet6 fe80::f27b:cbff:fe31:1a2d prefixlen 64 scopeid 0x20<link> ether f0:7b:cb:31:1a:2d txqueuelen 1000 (Ethernet) RX packets 1852 bytes 251822 (245.9 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 599 bytes 68026 (66.4 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Notez qu'en fonctionnement sans openvpn, le symbole du gestionnaire de connexion est :
Il évolue avec la connexion openvpn
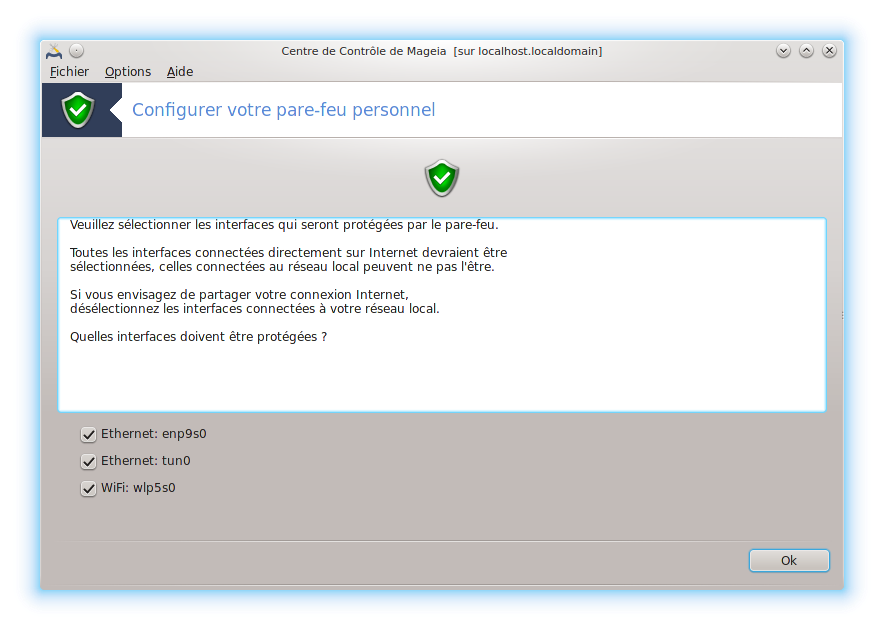
Notez que pour pouvoir me connecter au vpn, il m'a fallu désactiver le firewall via le centre de contrôle Mageia car celui ne connait pas l'interface tun0. En peut ensuite relancer le firewall une fois la connexion établie. Il reconnait l'interface tun0 et l'on peut la configurer correctement au niveau de drakfirewall.
Tout fonctionne, sauf qu'il y a un soucis de sécurité. Le système conserve l'ip du serveur dns de la connexion initiée par le wifi pour naviguer sur le net. Il ne tient pas compte du serveur dns communiqué par le serveur openvpn. Bref c'est pas top surtout quand on a des dns menteurs. Actuellement je n'ai pas trouvé la solution pour résoudre ce problème.
Édité par vouf Le 19/12/2015 à 11h23
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
Et si on essayait les outils Mageia...
En passant par les outils délivrés avec le centre de contrôle, après quelques tests, on obtient un résultat similaire..
J'ai installé le paquet opensc afin de faire disparaître un message d'erreur dans le syslog de mageia. Sinon, voici comment j'ai procédé.
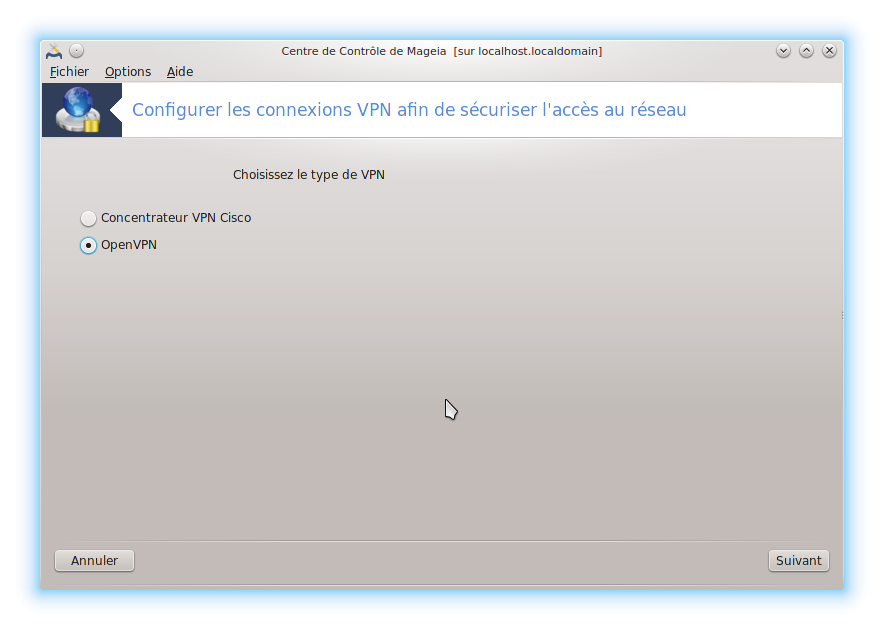
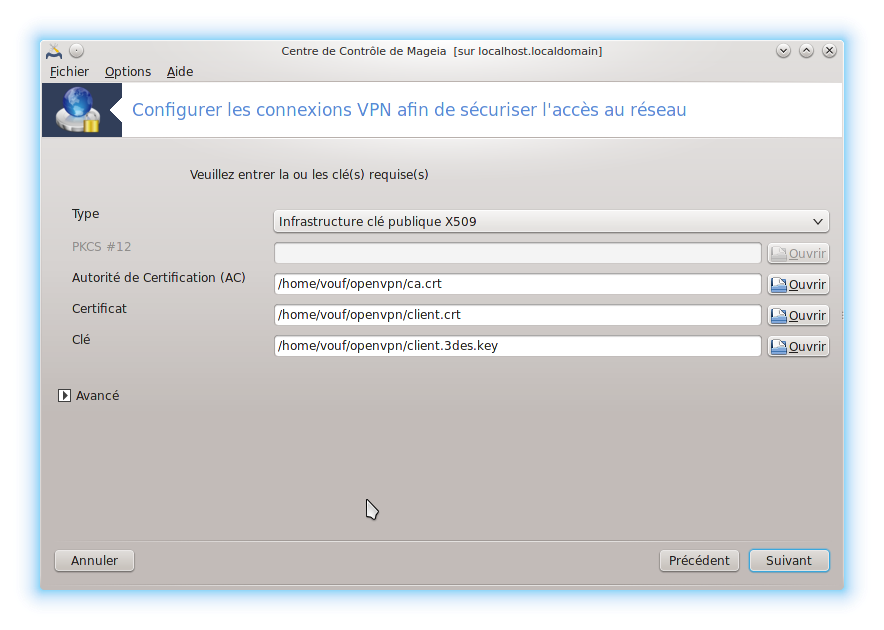
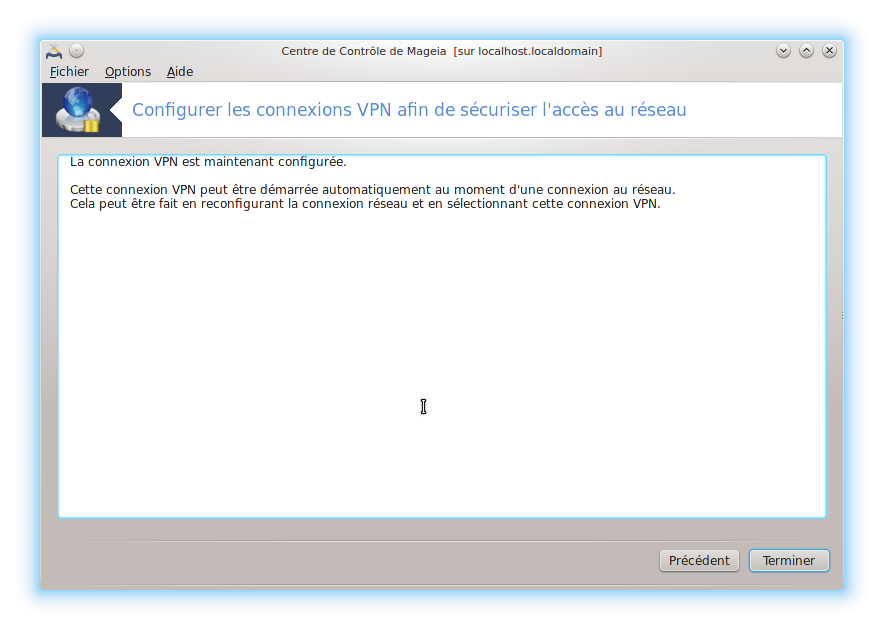
Il faut cliquer sur le bouton "Avancé" pour renseigner des options qui sont indispensables à la connexion.
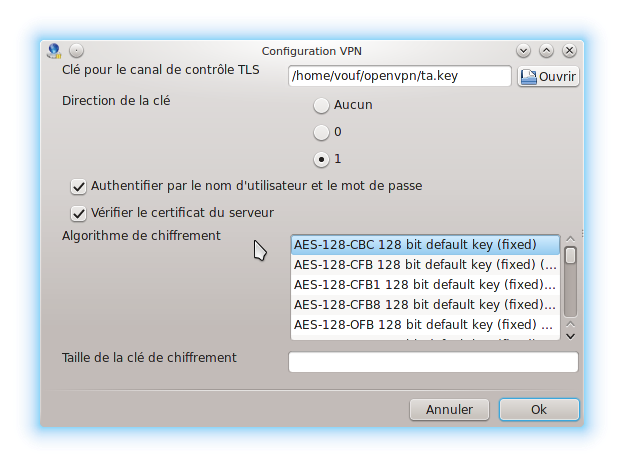
Pour déterminer l’algorithme de chiffrement, il faut regarder le contenu du fichier de configuration du client. Dans mon cas, j'ai cipher AES-128-CBC c'est pourquoi j'ai choisi AES 128-CBC 128 bits.
Notez que l'authentification ne fonctionnait pas si je n'avais pas une direction de clé à 1. C'est d'ailleurs indiqué dans le fichier de configuration du client "key-direction 1".
Le certificat du serveur par sécurité est vérifié. Je pense que c'est pour cela que le paquet opencs était nécessaire.
Il est nécessaire de cocher "Authentifier par le nom d'utilisateur et le mot de passe". Cela vous permettra de renseigner votre login (ici client) et votre mot de passe.
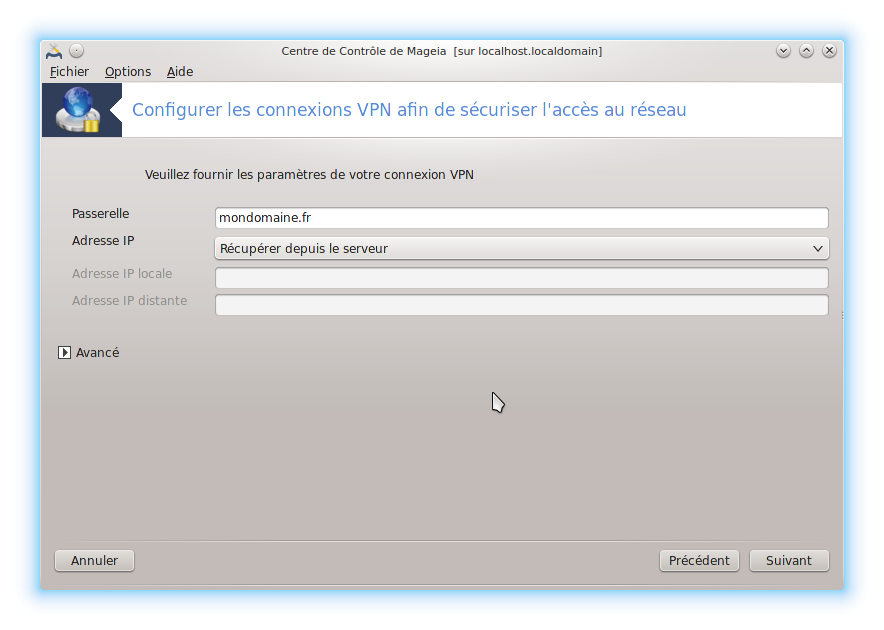
Il faut adapter le port de connexion. Par défaut, cela reste 1194. Par défaut , c'est en udp. Sinon il faut cocher tcp. Laissez tun pour la création de l'interface réseau.
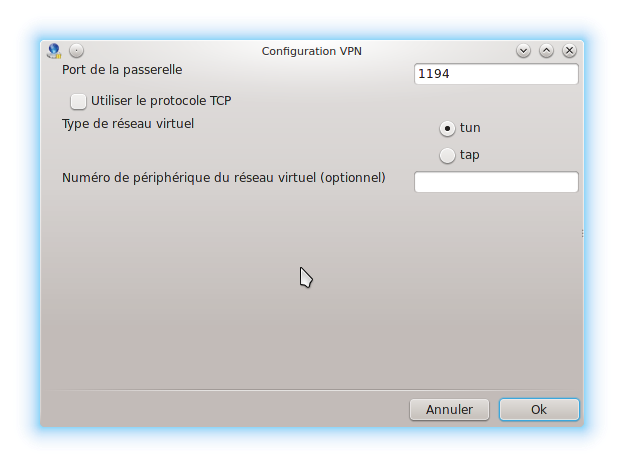
La connexion s'effectue ensuite. On vous demandera de saisir votre login et votre de mot de passe. Chez moi, on me le demande 2 fois. L'un pour la clé public, l'autre pour la clé privée. Dans mon cas les logins et mot de passe sont identiques.
Au niveau du syslog mageia j'ai :
Code TEXT :
Dec 19 13:03:05 localhost openvpn[5368]: OpenVPN 2.3.6 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Dec 27 2014 Dec 19 13:03:05 localhost openvpn[5368]: library versions: OpenSSL 1.0.2e 3 Dec 2015, LZO 2.09 Dec 19 13:03:05 localhost openvpn[5368]: MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:2222 Dec 19 13:03:05 localhost openvpn[5369]: Need password(s) from management interface, waiting... Dec 19 13:03:05 localhost openvpn[5369]: MANAGEMENT: Client connected from [AF_INET]127.0.0.1:2222 Dec 19 13:03:05 localhost openvpn[5369]: MANAGEMENT: CMD 'username "Auth" "client"' Dec 19 13:03:05 localhost openvpn[5369]: MANAGEMENT: CMD 'password [...]' Dec 19 13:03:05 localhost openvpn[5369]: MANAGEMENT: CMD 'username "Private Key" "client"' Dec 19 13:03:05 localhost openvpn[5369]: MANAGEMENT: CMD 'password [...]' Dec 19 13:03:05 localhost openvpn[5369]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Dec 19 13:03:05 localhost openvpn[7067]: WARNING: file '/home/vouf/openvpn/client.3des.key' is group or others accessible Dec 19 13:03:05 localhost openvpn[7067]: WARNING: file '/home/vouf/openvpn/ta.key' is group or others accessible Dec 19 13:03:05 localhost openvpn[7067]: Control Channel Authentication: using '/home/vouf/openvpn/ta.key' as a OpenVPN static key file Dec 19 13:03:05 localhost openvpn[7067]: Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Dec 19 13:03:05 localhost openvpn[7067]: Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Dec 19 13:03:05 localhost openvpn[7067]: Socket Buffers: R=[212992->131072] S=[212992->131072] Dec 19 13:03:05 localhost openvpn[7131]: NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay Dec 19 13:03:05 localhost openvpn[7131]: UDPv4 link local: [undef] Dec 19 13:03:05 localhost openvpn[7131]: UDPv4 link remote: [AF_INET]90.45.67.199:Dec 19 13:03:05 localhost openvpn[7131]: TLS: Initial packet from [AF_INET]90.45.67.199:1194, sid=665554a2 95d7d1ce Dec 19 13:03:06 localhost openvpn[7131]: VERIFY OK: depth=1, C=FR, ST=France, L=Triffouillis, O=Aquitaine, OU=SO, CN=Aquitaine CA, name=Vouf, emailAddress=.....com Dec 19 13:03:06 localhost openvpn[7131]: VERIFY OK: nsCertType=SERVER Dec 19 13:03:06 localhost openvpn[7131]: VERIFY OK: depth=0, C=FR, ST=France, L=Triffouillis, O=Aquitaine, OU=SO, CN=server, name=Vouf, emailAddress=......com Dec 19 13:03:07 localhost openvpn[7131]: Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key Dec 19 13:03:07 localhost openvpn[7131]: Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Dec 19 13:03:07 localhost openvpn[7131]: Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key Dec 19 13:03:07 localhost openvpn[7131]: Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Dec 19 13:03:07 localhost openvpn[7131]: Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA Dec 19 13:03:07 localhost openvpn[7131]: [server] Peer Connection Initiated with [AF_INET]90.45.66.199:1194 Dec 19 13:03:10 localhost openvpn[7131]: SENT CONTROL [server]: 'PUSH_REQUEST' (status=1) Dec 19 13:03:10 localhost openvpn[7131]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.8.0.1,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9' 1194
Côté serveur vpn
Code TEXT :
Sat Dec 19 13:03:05 2015 80.12.58.39:56593 TLS: Initial packet from [AF_INET]80.12.58.55:56593, sid=64665a68 e42f021f Sat Dec 19 13:03:07 2015 80.12.58.39:56593 VERIFY OK: depth=1, C=FR, ST=France, L=Triffouillis, O=Aquitaine, OU=SO, CN=Aquitaine CA, name=Vouf, emailAddress=...com Sat Dec 19 13:03:07 2015 80.12.58.39:56593 VERIFY OK: depth=0, C=FR, ST=France, L=Triffouillis, O=Aquitaine, OU=SO, CN=client, name=Vouf, emailAddress=...com Sat Dec 19 13:03:07 2015 80.12.58.39:56593 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key Sat Dec 19 13:03:07 2015 80.12.58.39:56593 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Sat Dec 19 13:03:07 2015 80.12.58.39:56593 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key Sat Dec 19 13:03:07 2015 80.12.58.39:56593 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Sat Dec 19 13:03:07 2015 80.12.58.39:56593 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA Sat Dec 19 13:03:07 2015 80.12.58.39:56593 [client] Peer Connection Initiated with [AF_INET]80.12.58.39:56593 Sat Dec 19 13:03:07 2015 client/80.12.58.39:56593 MULTI_sva: pool returned IPv4=10.8.0.10, IPv6=(Not enabled) Sat Dec 19 13:03:07 2015 client/80.12.58.39:56593 MULTI: Learn: 10.8.0.10 -> client/80.12.58.39:56593 Sat Dec 19 13:03:07 2015 client/80.12.58.39:56593 MULTI: primary virtual IP for client/80.12.58.55:56593: 10.8.0.10 Sat Dec 19 13:03:10 2015 client/80.12.58.39:56593 PUSH: Received control message: 'PUSH_REQUEST' Sat Dec 19 13:03:10 2015 client/80.12.58.39:56593 send_push_reply(): safe_cap=940 Sat Dec 19 13:03:10 2015 client/80.12.58.39:56593 SENT CONTROL [client]: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.8.0.1,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.10 10.8.0.9' (status=1)
Comme dans le post précédent, la gestion du dns n'est pas correctement prise en compte. Le plus simple est d'ajouter dans le fichier /etc/resolv.conf l'ip du serveur dns, c'est à dire dans mon cas 10.8.0.1. On le met en tête et conserve le dns du wifi dessous.
J'espère que ce post vous sera utile. Je dois dire que j'ai trouvé sur le net très peu d'informations sur openvpn et mageia.....
Édité par vouf Le 19/12/2015 à 14h59
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
zwykx Membre non connecté
-

- Voir le profil du membre zwykx
- Inscrit le : 21/01/2013
- Groupes :
Je galère depuis plusieurs jours pour arriver à connecter un client openvpn sur un serveur de Vpnbook.
J'utilise la ligne de commande pour démarrer le client et tout a l'air de bien se passer :
# openvpn --config /home/moi/Logiciels/Internet/VPNBook.com-OpenVPN-Euro1/vpnbook-euro1-udp53.ovpn --auth-user-pass /home/moi/Logiciels/Internet/VPNBook.com-OpenVPN-Euro1/id.txt
Mon Aug 1 12:19:34 2016 OpenVPN 2.3.11 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on May 17 2016
Mon Aug 1 12:19:34 2016 library versions: OpenSSL 1.0.2h 3 May 2016, LZO 2.09
Mon Aug 1 12:19:34 2016 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Mon Aug 1 12:19:34 2016 Socket Buffers: R=[212992->212992] S=[212992->212992]
Mon Aug 1 12:19:34 2016 UDPv4 link local: [undef]
Mon Aug 1 12:19:34 2016 UDPv4 link remote: [AF_INET]176.126.237.217:53
Mon Aug 1 12:19:34 2016 TLS: Initial packet from [AF_INET]176.126.237.217:53, sid=1126e8d2 c22358d5
Mon Aug 1 12:19:34 2016 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Mon Aug 1 12:19:35 2016 VERIFY OK: depth=1, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 12:19:35 2016 VERIFY OK: depth=0, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 12:19:35 2016 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 12:19:35 2016 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 12:19:35 2016 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 12:19:35 2016 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 12:19:35 2016 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Mon Aug 1 12:19:35 2016 [vpnbook.com] Peer Connection Initiated with [AF_INET]176.126.237.217:53
Mon Aug 1 12:19:37 2016 SENT CONTROL [vpnbook.com]: 'PUSH_REQUEST' (status=1)
Mon Aug 1 12:19:37 2016 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 89.233.43.71,dhcp-option DNS 91.239.100.100,route 10.8.0.1,topology net30,ping 5,ping-restart 30,ifconfig 10.8.0.166 10.8.0.165'
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: timers and/or timeouts modified
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: --ifconfig/up options modified
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: route options modified
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Mon Aug 1 12:19:37 2016 ROUTE_GATEWAY 192.168.0.254/255.255.255.0 IFACE=eth0 HWADDR=bc:ae:c5:5b:c2:8c
Mon Aug 1 12:19:37 2016 TUN/TAP device tun0 opened
Mon Aug 1 12:19:37 2016 TUN/TAP TX queue length set to 100
Mon Aug 1 12:19:37 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Aug 1 12:19:37 2016 /usr/sbin/ifconfig tun0 10.8.0.166 pointopoint 10.8.0.165 mtu 1500
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 176.126.237.217 netmask 255.255.255.255 gw 192.168.0.254
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.165
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.8.0.165
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 10.8.0.1 netmask 255.255.255.255 gw 10.8.0.165
Mon Aug 1 12:19:40 2016 Initialization Sequence Completed
Mon Aug 1 12:19:34 2016 OpenVPN 2.3.11 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on May 17 2016
Mon Aug 1 12:19:34 2016 library versions: OpenSSL 1.0.2h 3 May 2016, LZO 2.09
Mon Aug 1 12:19:34 2016 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Mon Aug 1 12:19:34 2016 Socket Buffers: R=[212992->212992] S=[212992->212992]
Mon Aug 1 12:19:34 2016 UDPv4 link local: [undef]
Mon Aug 1 12:19:34 2016 UDPv4 link remote: [AF_INET]176.126.237.217:53
Mon Aug 1 12:19:34 2016 TLS: Initial packet from [AF_INET]176.126.237.217:53, sid=1126e8d2 c22358d5
Mon Aug 1 12:19:34 2016 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Mon Aug 1 12:19:35 2016 VERIFY OK: depth=1, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 12:19:35 2016 VERIFY OK: depth=0, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 12:19:35 2016 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 12:19:35 2016 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 12:19:35 2016 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 12:19:35 2016 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 12:19:35 2016 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Mon Aug 1 12:19:35 2016 [vpnbook.com] Peer Connection Initiated with [AF_INET]176.126.237.217:53
Mon Aug 1 12:19:37 2016 SENT CONTROL [vpnbook.com]: 'PUSH_REQUEST' (status=1)
Mon Aug 1 12:19:37 2016 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 89.233.43.71,dhcp-option DNS 91.239.100.100,route 10.8.0.1,topology net30,ping 5,ping-restart 30,ifconfig 10.8.0.166 10.8.0.165'
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: timers and/or timeouts modified
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: --ifconfig/up options modified
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: route options modified
Mon Aug 1 12:19:37 2016 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Mon Aug 1 12:19:37 2016 ROUTE_GATEWAY 192.168.0.254/255.255.255.0 IFACE=eth0 HWADDR=bc:ae:c5:5b:c2:8c
Mon Aug 1 12:19:37 2016 TUN/TAP device tun0 opened
Mon Aug 1 12:19:37 2016 TUN/TAP TX queue length set to 100
Mon Aug 1 12:19:37 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Aug 1 12:19:37 2016 /usr/sbin/ifconfig tun0 10.8.0.166 pointopoint 10.8.0.165 mtu 1500
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 176.126.237.217 netmask 255.255.255.255 gw 192.168.0.254
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.165
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.8.0.165
Mon Aug 1 12:19:40 2016 /usr/sbin/route add -net 10.8.0.1 netmask 255.255.255.255 gw 10.8.0.165
Mon Aug 1 12:19:40 2016 Initialization Sequence Completed
Il me crée bien une nouvelle interface réseau tun0 :
# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.1 netmask 255.255.255.0 broadcast 192.168.0.255
inet6 fe80::beae:c5ff:fe5b:c28c prefixlen 64 scopeid 0x20<link>
ether bc:ae:c5:5b:c2:8c txqueuelen 1000 (Ethernet)
RX packets 6548994 bytes 8727801956 (8.1 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 860725 bytes 98267990 (93.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Boucle locale)
RX packets 844033 bytes 286320450 (273.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 844033 bytes 286320450 (273.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.8.0.198 netmask 255.255.255.255 destination 10.8.0.197
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.1 netmask 255.255.255.0 broadcast 192.168.0.255
inet6 fe80::beae:c5ff:fe5b:c28c prefixlen 64 scopeid 0x20<link>
ether bc:ae:c5:5b:c2:8c txqueuelen 1000 (Ethernet)
RX packets 6548994 bytes 8727801956 (8.1 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 860725 bytes 98267990 (93.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Boucle locale)
RX packets 844033 bytes 286320450 (273.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 844033 bytes 286320450 (273.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.8.0.198 netmask 255.255.255.255 destination 10.8.0.197
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
J'ai déclaré tun0 dans /etc/shorewall/interfaces donc je n'ai plus d'erreur au niveau firewall.
Mais quand j'ouvre un navigateur, rien ne se passe, il cherche l'URL indéfiniement !
Aurait-tu une idée du problème en question ?
Merci.
PC : Z80 SoftCard, CPU Z80, 64 K RAM
zwykx Membre non connecté
-

- Voir le profil du membre zwykx
- Inscrit le : 21/01/2013
- Groupes :
Après avoir installé les dernières mises à jour (noyau, glibc) avec le MCC, puis rebooté, j'obtiens :
# openvpn --config /home/moi/Logiciels/Internet/VPNBook.com-OpenVPN-Euro1/vpnbook-euro1-udp53.ovpn --auth-user-pass /home/moi/Logiciels/Internet/VPNBook.com-OpenVPN-Euro1/id.txt
Mon Aug 1 18:50:42 2016 OpenVPN 2.3.11 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on May 17 2016
Mon Aug 1 18:50:42 2016 library versions: OpenSSL 1.0.2h 3 May 2016, LZO 2.09
Mon Aug 1 18:50:42 2016 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Mon Aug 1 18:50:42 2016 Socket Buffers: R=[212992->212992] S=[212992->212992]
Mon Aug 1 18:50:42 2016 UDPv4 link local: [undef]
Mon Aug 1 18:50:42 2016 UDPv4 link remote: [AF_INET]176.126.237.217:53
Mon Aug 1 18:50:43 2016 TLS: Initial packet from [AF_INET]176.126.237.217:53, sid=39d8abec cf9a2a5f
Mon Aug 1 18:50:43 2016 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Mon Aug 1 18:50:43 2016 VERIFY OK: depth=1, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 18:50:43 2016 VERIFY OK: depth=0, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 18:50:43 2016 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 18:50:43 2016 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 18:50:43 2016 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 18:50:43 2016 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 18:50:43 2016 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Mon Aug 1 18:50:43 2016 [vpnbook.com] Peer Connection Initiated with [AF_INET]176.126.237.217:53
Mon Aug 1 18:50:46 2016 SENT CONTROL [vpnbook.com]: 'PUSH_REQUEST' (status=1)
Mon Aug 1 18:50:46 2016 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 89.233.43.71,dhcp-option DNS 91.239.100.100,route 10.8.0.1,topology net30,ping 5,ping-restart 30,ifconfig 10.8.0.118 10.8.0.117'
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: timers and/or timeouts modified
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: --ifconfig/up options modified
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: route options modified
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Mon Aug 1 18:50:46 2016 ROUTE_GATEWAY 192.168.0.254/255.255.255.0 IFACE=eth0 HWADDR=bc:ae:c5:5b:c2:8c
Mon Aug 1 18:50:46 2016 TUN/TAP device tun0 opened
Mon Aug 1 18:50:46 2016 TUN/TAP TX queue length set to 100
Mon Aug 1 18:50:46 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Aug 1 18:50:46 2016 /usr/sbin/ifconfig tun0 10.8.0.118 pointopoint 10.8.0.117 mtu 1500
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 176.126.237.217 netmask 255.255.255.255 gw 192.168.0.254
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.117
SIOCADDRT: Network is unreachable
Mon Aug 1 18:50:48 2016 ERROR: Linux route add command failed: external program exited with error status: 7
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.8.0.117
SIOCADDRT: Network is unreachable
Mon Aug 1 18:50:48 2016 ERROR: Linux route add command failed: external program exited with error status: 7
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 10.8.0.1 netmask 255.255.255.255 gw 10.8.0.117
SIOCADDRT: Network is unreachable
Mon Aug 1 18:50:48 2016 ERROR: Linux route add command failed: external program exited with error status: 7
Mon Aug 1 18:50:48 2016 Initialization Sequence Completed
Mon Aug 1 18:50:42 2016 OpenVPN 2.3.11 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on May 17 2016
Mon Aug 1 18:50:42 2016 library versions: OpenSSL 1.0.2h 3 May 2016, LZO 2.09
Mon Aug 1 18:50:42 2016 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Mon Aug 1 18:50:42 2016 Socket Buffers: R=[212992->212992] S=[212992->212992]
Mon Aug 1 18:50:42 2016 UDPv4 link local: [undef]
Mon Aug 1 18:50:42 2016 UDPv4 link remote: [AF_INET]176.126.237.217:53
Mon Aug 1 18:50:43 2016 TLS: Initial packet from [AF_INET]176.126.237.217:53, sid=39d8abec cf9a2a5f
Mon Aug 1 18:50:43 2016 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Mon Aug 1 18:50:43 2016 VERIFY OK: depth=1, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 18:50:43 2016 VERIFY OK: depth=0, C=CH, ST=Zurich, L=Zurich, O=vpnbook.com, OU=IT, CN=vpnbook.com, name=vpnbook.com, emailAddress=admin@vpnbook.com
Mon Aug 1 18:50:43 2016 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 18:50:43 2016 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 18:50:43 2016 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Mon Aug 1 18:50:43 2016 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Mon Aug 1 18:50:43 2016 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Mon Aug 1 18:50:43 2016 [vpnbook.com] Peer Connection Initiated with [AF_INET]176.126.237.217:53
Mon Aug 1 18:50:46 2016 SENT CONTROL [vpnbook.com]: 'PUSH_REQUEST' (status=1)
Mon Aug 1 18:50:46 2016 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 89.233.43.71,dhcp-option DNS 91.239.100.100,route 10.8.0.1,topology net30,ping 5,ping-restart 30,ifconfig 10.8.0.118 10.8.0.117'
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: timers and/or timeouts modified
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: --ifconfig/up options modified
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: route options modified
Mon Aug 1 18:50:46 2016 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Mon Aug 1 18:50:46 2016 ROUTE_GATEWAY 192.168.0.254/255.255.255.0 IFACE=eth0 HWADDR=bc:ae:c5:5b:c2:8c
Mon Aug 1 18:50:46 2016 TUN/TAP device tun0 opened
Mon Aug 1 18:50:46 2016 TUN/TAP TX queue length set to 100
Mon Aug 1 18:50:46 2016 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Mon Aug 1 18:50:46 2016 /usr/sbin/ifconfig tun0 10.8.0.118 pointopoint 10.8.0.117 mtu 1500
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 176.126.237.217 netmask 255.255.255.255 gw 192.168.0.254
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.117
SIOCADDRT: Network is unreachable
Mon Aug 1 18:50:48 2016 ERROR: Linux route add command failed: external program exited with error status: 7
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.8.0.117
SIOCADDRT: Network is unreachable
Mon Aug 1 18:50:48 2016 ERROR: Linux route add command failed: external program exited with error status: 7
Mon Aug 1 18:50:48 2016 /usr/sbin/route add -net 10.8.0.1 netmask 255.255.255.255 gw 10.8.0.117
SIOCADDRT: Network is unreachable
Mon Aug 1 18:50:48 2016 ERROR: Linux route add command failed: external program exited with error status: 7
Mon Aug 1 18:50:48 2016 Initialization Sequence Completed
et tun0 n'a pas d'adresse :
# ifconfig tun0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Si j'exécute manuellement :
/usr/sbin/ifconfig tun0 10.8.0.118 pointopoint 10.8.0.117 mtu 1500
Cette fois-ci, ça passe :
# ifconfig tun0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.8.0.118 netmask 255.255.255.255 destination 10.8.0.117
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 9 bytes 685 (685.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.8.0.118 netmask 255.255.255.255 destination 10.8.0.117
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 9 bytes 685 (685.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
et la table de routage est :
# route
Table de routage IP du noyau
Destination Passerelle Genmask Indic Metric Ref Use Iface
default 192.168.0.254 0.0.0.0 UG 10 0 0 eth0
10.8.0.117 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
link-local 0.0.0.0 255.255.0.0 U 10 0 0 eth0
euro217.vpnbook 192.168.0.254 255.255.255.255 UGH 0 0 0 eth0
24.157.33.178.r 192.168.0.254 255.255.255.255 UGH 0 0 0 eth0
192.168.0.0 0.0.0.0 255.255.255.0 U 10 0 0 eth0
Table de routage IP du noyau
Destination Passerelle Genmask Indic Metric Ref Use Iface
default 192.168.0.254 0.0.0.0 UG 10 0 0 eth0
10.8.0.117 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
link-local 0.0.0.0 255.255.0.0 U 10 0 0 eth0
euro217.vpnbook 192.168.0.254 255.255.255.255 UGH 0 0 0 eth0
24.157.33.178.r 192.168.0.254 255.255.255.255 UGH 0 0 0 eth0
192.168.0.0 0.0.0.0 255.255.255.0 U 10 0 0 eth0
mais mon IP n'a pas changée.
par contre si j'ajoute une route :
Citation :
/usr/sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.117
mon IP devient celle de euro217.vpnbook.com et je peux naviguer à travers le VPN.
Donc il semble qu'il y ait 2 problèmes :
1 - openvpn génère des erreurs (notamment la configuration de tun0)
2 - openvpm crée par défaut une table de routage qui ne fonctionne pas
Qu'en pensent les spécialistes ?
Édité par zwykx Le 01/08/2016 à 19h13
PC : Z80 SoftCard, CPU Z80, 64 K RAM
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
Pour le problème se situe autours de la résolution de nom quand tu es connecté sur ton vpn. Dans le fichier /etc/resolv.conf remplace ou ajoute une ligne avec nameserver 10.8.0.1 pour voir pour que ce soit le server vpn qui fasse la résolution de nom
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
zwykx Membre non connecté
-

- Voir le profil du membre zwykx
- Inscrit le : 21/01/2013
- Groupes :
J'ai essayé de rajouter un DNS mais sans succès
PC : Z80 SoftCard, CPU Z80, 64 K RAM
xuo Membre non connecté
-

- Voir le profil du membre xuo
- Inscrit le : 23/10/2011
- Groupes :
Je repars de ce post car il m'a bien aidé pour essayer de démarrer ma connexion vpn même si pour le moment je n'arrive pas à la faire fonctionner.
Je suis parti de ce qui est décrit à cette adresse (https://open-freax.fr/monter-vpn-openvpn), puis de ce que Vouf a fait (il y a des différences dans la config du serveur).
Dans les 2 cas, ma config du client est la même. seule celle du serveur change.
Voici ce que j'obtiens :
Config1 : source = https://open-freax.fr/monter-vpn-openvpn
serveur :
adresse IP locale : 192.168.0.14
config serveur :
Caché:
# adresse locale du serveur
local 192.168.0.14
# type d'interface
dev tun
# protocole de communication
proto udp
# numéro du port utilisé
port 1194
# emplacement du master CA
ca /etc/openvpn/easy-rsa/keys/ca.crt
# emplacement du certificat du serveur
cert /etc/openvpn/easy-rsa/keys/freexuo_vpn.crt
# emplacement de la clé du serveur
key /etc/openvpn/easy-rsa/keys/freexuo_vpn.key
# emplacement du fichier Diffie-Hellman
dh /etc/openvpn/easy-rsa/keys/dh2048.pem
# quelle sera l'adresse du réseau virtuel créé par le VPN
# l'adresse du serveur VPN
server 10.8.0.0 255.255.255.0
# serveur et point de sortie distant
ifconfig 10.8.0.1 10.8.0.2
push "redirect-gateway def1"
push "route 10.8.0.1 255.255.255.255" # route vers le serveur VPN
push "route 10.8.0.0 255.255.255.0" # route vers le sous-réseau VPN
push "route 192.168.0.14 255.255.255.0" #sous-réseau local - adaptez l'adresse IP locale de votre serveur
push "dhcp-option DNS 192.168.0.1" # votre serveur DNS primaire (votre routeur, souvent)
#push "route 192.168.0.0 255.255.255.0"
#push "redirect-gateway def1 bypass-dhcp"
client-to-client
duplicate-cn
tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0
#
keepalive 10 120
#type d'encryptage des données
cipher AES-128-CBC
#activation de la compression
comp-lzo
#nombre maximum de clients autorisés
max-clients 2
#pas d'utilisateur et groupe particuliers pour l'utilisation du VPN
user nobody
group nobody
#pour rendre la connexion persistante
persist-key
persist-tun
#fichier de log
status /var/log/openvpn-status.log 20
log /var/log/openvpn.log
# niveau de verbosité
verb 5
local 192.168.0.14
# type d'interface
dev tun
# protocole de communication
proto udp
# numéro du port utilisé
port 1194
# emplacement du master CA
ca /etc/openvpn/easy-rsa/keys/ca.crt
# emplacement du certificat du serveur
cert /etc/openvpn/easy-rsa/keys/freexuo_vpn.crt
# emplacement de la clé du serveur
key /etc/openvpn/easy-rsa/keys/freexuo_vpn.key
# emplacement du fichier Diffie-Hellman
dh /etc/openvpn/easy-rsa/keys/dh2048.pem
# quelle sera l'adresse du réseau virtuel créé par le VPN
# l'adresse du serveur VPN
server 10.8.0.0 255.255.255.0
# serveur et point de sortie distant
ifconfig 10.8.0.1 10.8.0.2
push "redirect-gateway def1"
push "route 10.8.0.1 255.255.255.255" # route vers le serveur VPN
push "route 10.8.0.0 255.255.255.0" # route vers le sous-réseau VPN
push "route 192.168.0.14 255.255.255.0" #sous-réseau local - adaptez l'adresse IP locale de votre serveur
push "dhcp-option DNS 192.168.0.1" # votre serveur DNS primaire (votre routeur, souvent)
#push "route 192.168.0.0 255.255.255.0"
#push "redirect-gateway def1 bypass-dhcp"
client-to-client
duplicate-cn
tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0
#
keepalive 10 120
#type d'encryptage des données
cipher AES-128-CBC
#activation de la compression
comp-lzo
#nombre maximum de clients autorisés
max-clients 2
#pas d'utilisateur et groupe particuliers pour l'utilisation du VPN
user nobody
group nobody
#pour rendre la connexion persistante
persist-key
persist-tun
#fichier de log
status /var/log/openvpn-status.log 20
log /var/log/openvpn.log
# niveau de verbosité
verb 5
Client :
adresse IP : 192.168.1.99
Passerelle : 192.168.1.254
DNS : 192.168.1.254
ip = ip_de_ordi_de_pascale
Caché:
#pour signaler que c'est un client !
client
#type d'interface
dev tun
#protocole de communication
proto udp
#adresse ip publique du réseau dans lequel le serveur est installe + port identique au serveur
remote xuo.fr 1194
#tentative de connexion infinie
resolv-retry infinite
nobind
#pour rendre la connexion persistante
persist-key
persist-tun
#pour cacher les avertissements
mute-replay-warnings
#emplacement du master CA
ca /etc/openvpn/easy-rsa/keys/ca.crt
#emplacement du certificat client
cert /etc/openvpn/easy-rsa/keys/ordi_de_pascale.crt
#emplacement de la cle privee du client
key /etc/openvpn/easy-rsa/keys/ordi_de_pascale.key
#type d'encryptage des données
cipher AES-128-CBC
#activation de la compression
comp-lzo
#niveau de verbosité
verb 5
status openvpn-status.log
log openvpn.log
client
#type d'interface
dev tun
#protocole de communication
proto udp
#adresse ip publique du réseau dans lequel le serveur est installe + port identique au serveur
remote xuo.fr 1194
#tentative de connexion infinie
resolv-retry infinite
nobind
#pour rendre la connexion persistante
persist-key
persist-tun
#pour cacher les avertissements
mute-replay-warnings
#emplacement du master CA
ca /etc/openvpn/easy-rsa/keys/ca.crt
#emplacement du certificat client
cert /etc/openvpn/easy-rsa/keys/ordi_de_pascale.crt
#emplacement de la cle privee du client
key /etc/openvpn/easy-rsa/keys/ordi_de_pascale.key
#type d'encryptage des données
cipher AES-128-CBC
#activation de la compression
comp-lzo
#niveau de verbosité
verb 5
status openvpn-status.log
log openvpn.log
Résultats de la config 1 :
Serveur :
Caché:
Tue May 30 19:22:27 2017 us=853666 tcp_queue_limit = 64
Tue May 30 19:22:27 2017 us=853672 real_hash_size = 256
Tue May 30 19:22:27 2017 us=853678 virtual_hash_size = 256
Tue May 30 19:22:27 2017 us=853684 client_connect_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853690 learn_address_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853696 client_disconnect_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853702 client_config_dir = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853708 ccd_exclusive = DISABLED
Tue May 30 19:22:27 2017 us=853714 tmp_dir = '/root/tmp'
Tue May 30 19:22:27 2017 us=853720 push_ifconfig_defined = DISABLED
Tue May 30 19:22:27 2017 us=853727 push_ifconfig_local = 0.0.0.0
Tue May 30 19:22:27 2017 us=853733 push_ifconfig_remote_netmask = 0.0.0.0
Tue May 30 19:22:27 2017 us=853739 push_ifconfig_ipv6_defined = DISABLED
Tue May 30 19:22:27 2017 us=853746 push_ifconfig_ipv6_local = ::/0
Tue May 30 19:22:27 2017 us=853752 push_ifconfig_ipv6_remote = ::
Tue May 30 19:22:27 2017 us=853758 enable_c2c = ENABLED
Tue May 30 19:22:27 2017 us=853764 duplicate_cn = ENABLED
Tue May 30 19:22:27 2017 us=853770 cf_max = 0
Tue May 30 19:22:27 2017 us=853776 cf_per = 0
Tue May 30 19:22:27 2017 us=853782 max_clients = 2
Tue May 30 19:22:27 2017 us=853787 max_routes_per_client = 256
Tue May 30 19:22:27 2017 us=853793 auth_user_pass_verify_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853799 auth_user_pass_verify_script_via_file = DISABLED
Tue May 30 19:22:27 2017 us=853805 port_share_host = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853811 port_share_port = 0
Tue May 30 19:22:27 2017 us=853817 client = DISABLED
Tue May 30 19:22:27 2017 us=853823 pull = DISABLED
Tue May 30 19:22:27 2017 us=853829 auth_user_pass_file = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853836 OpenVPN 2.3.12 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Aug 26 2016
Tue May 30 19:22:27 2017 us=853848 library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.09
Tue May 30 19:22:27 2017 us=853957 NOTE: your local LAN uses the extremely common subnet address 192.168.0.x or 192.168.1.x. Be aware that this might create routing conflicts if you connect to the VPN server from public locations such as internet cafes that use the same subnet.
Tue May 30 19:22:27 2017 us=871320 Diffie-Hellman initialized with 2048 bit key
Tue May 30 19:22:27 2017 us=881102 Control Channel Authentication: using '/etc/openvpn/easy-rsa/keys/ta.key' as a OpenVPN static key file
Tue May 30 19:22:27 2017 us=881147 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:22:27 2017 us=881162 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:22:27 2017 us=881184 TLS-Auth MTU parms [ L:1558 D:1184 EF:66 EB:0 ET:0 EL:3 ]
Tue May 30 19:22:27 2017 us=881205 Socket Buffers: R=[212992->212992] S=[212992->212992]
Tue May 30 19:22:27 2017 us=881326 ROUTE_GATEWAY 192.168.0.1/255.255.255.0 IFACE=enp4s0 HWADDR=80:ee:73:63:54:a6
Tue May 30 19:22:27 2017 us=882327 TUN/TAP device tun0 opened
Tue May 30 19:22:27 2017 us=882387 TUN/TAP TX queue length set to 100
Tue May 30 19:22:27 2017 us=882407 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue May 30 19:22:27 2017 us=882437 /usr/sbin/ifconfig tun0 10.8.0.1 pointopoint 10.8.0.2 mtu 1500
Tue May 30 19:22:27 2017 us=885103 /usr/sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
Tue May 30 19:22:27 2017 us=885780 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:143 ET:0 EL:3 AF:3/1 ]
Tue May 30 19:22:27 2017 us=886045 GID set to nobody
Tue May 30 19:22:27 2017 us=886066 UID set to nobody
Tue May 30 19:22:27 2017 us=886080 UDPv4 link local (bound): [AF_INET]192.168.0.14:1194
Tue May 30 19:22:27 2017 us=886087 UDPv4 link remote: [undef]
Tue May 30 19:22:27 2017 us=886097 MULTI: multi_init called, r=256 v=256
Tue May 30 19:22:27 2017 us=886120 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Tue May 30 19:22:27 2017 us=886143 Initialization Sequence Completed
Tue May 30 19:22:52 2017 us=105110 MULTI: multi_create_instance called
Tue May 30 19:22:52 2017 us=105183 ip_de_ordi_de_pascale:41256 Re-using SSL/TLS context
Tue May 30 19:22:52 2017 us=105214 ip_de_ordi_de_pascale:41256 LZO compression initialized
Tue May 30 19:22:52 2017 us=105281 ip_de_ordi_de_pascale:41256 Control Channel MTU parms [ L:1558 D:1184 EF:66 EB:0 ET:0 EL:3 ]
Tue May 30 19:22:52 2017 us=105292 ip_de_ordi_de_pascale:41256 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:143 ET:0 EL:3 AF:3/1 ]
Tue May 30 19:22:52 2017 us=105313 ip_de_ordi_de_pascale:41256 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-server'
Tue May 30 19:22:52 2017 us=105320 ip_de_ordi_de_pascale:41256 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-client'
Tue May 30 19:22:52 2017 us=105334 ip_de_ordi_de_pascale:41256 Local Options hash (VER=V4): 'a2e63101'
Tue May 30 19:22:52 2017 us=105344 ip_de_ordi_de_pascale:41256 Expected Remote Options hash (VER=V4): '272f1b58'
RTue May 30 19:22:52 2017 us=105375 ip_de_ordi_de_pascale:41256 TLS: Initial packet from [AF_INET]ip_de_ordi_de_pascale:41256, sid=90ff2062 04b02a1c
WRRWWWWRRRRWRWRTue May 30 19:22:52 2017 us=243713 ip_de_ordi_de_pascale:41256 VERIFY OK: depth=1, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=freexuo_vpn, name=EB, emailAddress=eric@famille-bouyoux.fr
Tue May 30 19:22:52 2017 us=243854 ip_de_ordi_de_pascale:41256 VERIFY OK: depth=0, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=ordi_de_pascale, name=EB, emailAddress=eric@famille-bouyoux.fr
WRTue May 30 19:22:52 2017 us=286311 ip_de_ordi_de_pascale:41256 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:22:52 2017 us=286340 ip_de_ordi_de_pascale:41256 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:22:52 2017 us=286349 ip_de_ordi_de_pascale:41256 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:22:52 2017 us=286358 ip_de_ordi_de_pascale:41256 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
WRTue May 30 19:22:52 2017 us=321704 ip_de_ordi_de_pascale:41256 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Tue May 30 19:22:52 2017 us=321735 ip_de_ordi_de_pascale:41256 [ordi_de_pascale] Peer Connection Initiated with [AF_INET]ip_de_ordi_de_pascale:41256
Tue May 30 19:22:52 2017 us=321755 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
Tue May 30 19:22:52 2017 us=321786 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: Learn: 10.8.0.6 -> ordi_de_pascale/ip_de_ordi_de_pascale:41256
Tue May 30 19:22:52 2017 us=321795 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: primary virtual IP for ordi_de_pascale/ip_de_ordi_de_pascale:41256: 10.8.0.6
RTue May 30 19:22:54 2017 us=698333 ordi_de_pascale/ip_de_ordi_de_pascale:41256 PUSH: Received control message: 'PUSH_REQUEST'
Tue May 30 19:22:54 2017 us=698361 ordi_de_pascale/ip_de_ordi_de_pascale:41256 send_push_reply(): safe_cap=940
Tue May 30 19:22:54 2017 us=698386 ordi_de_pascale/ip_de_ordi_de_pascale:41256 SENT CONTROL [ordi_de_pascale]: 'PUSH_REPLY,redirect-gateway def1,route 10.8.0.1 255.255.255.255,route 10.8.0.0 255.255.255.0,route 192.168.0.14 255.255.255.0,dhcp-option DNS 192.168.0.1,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5' (status=1)
WWRRTue May 30 19:22:55 2017 us=743118 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:55 2017 us=940343 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:55 2017 us=978624 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:56 2017 us=216099 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:56 2017 us=423389 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:56 2017 us=693402 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:56 2017 us=910110 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:57 2017 us=640674 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:57 2017 us=884102 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:59 2017 us=541153 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:59 2017 us=833383 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:00 2017 us=741660 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:01 2017 us=126909 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:02 2017 us=129474 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:03 2017 us=130996 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:23:03 2017 us=336434 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRTue May 30 19:23:03 2017 us=729505 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:04 2017 us=133243 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
WRwRwRTue May 30 19:23:05 2017 us=135004 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:05 2017 us=940781 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRwRwRwRwRwRwRwRwRwRTue May 30 19:23:10 2017 us=936692 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRTue May 30 19:23:11 2017 us=528077 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRwRwRWwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRWwRwRwRTue May 30 19:23:26 2017 us=120723 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:27 2017 us=112934 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
Tue May 30 19:22:27 2017 us=853672 real_hash_size = 256
Tue May 30 19:22:27 2017 us=853678 virtual_hash_size = 256
Tue May 30 19:22:27 2017 us=853684 client_connect_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853690 learn_address_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853696 client_disconnect_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853702 client_config_dir = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853708 ccd_exclusive = DISABLED
Tue May 30 19:22:27 2017 us=853714 tmp_dir = '/root/tmp'
Tue May 30 19:22:27 2017 us=853720 push_ifconfig_defined = DISABLED
Tue May 30 19:22:27 2017 us=853727 push_ifconfig_local = 0.0.0.0
Tue May 30 19:22:27 2017 us=853733 push_ifconfig_remote_netmask = 0.0.0.0
Tue May 30 19:22:27 2017 us=853739 push_ifconfig_ipv6_defined = DISABLED
Tue May 30 19:22:27 2017 us=853746 push_ifconfig_ipv6_local = ::/0
Tue May 30 19:22:27 2017 us=853752 push_ifconfig_ipv6_remote = ::
Tue May 30 19:22:27 2017 us=853758 enable_c2c = ENABLED
Tue May 30 19:22:27 2017 us=853764 duplicate_cn = ENABLED
Tue May 30 19:22:27 2017 us=853770 cf_max = 0
Tue May 30 19:22:27 2017 us=853776 cf_per = 0
Tue May 30 19:22:27 2017 us=853782 max_clients = 2
Tue May 30 19:22:27 2017 us=853787 max_routes_per_client = 256
Tue May 30 19:22:27 2017 us=853793 auth_user_pass_verify_script = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853799 auth_user_pass_verify_script_via_file = DISABLED
Tue May 30 19:22:27 2017 us=853805 port_share_host = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853811 port_share_port = 0
Tue May 30 19:22:27 2017 us=853817 client = DISABLED
Tue May 30 19:22:27 2017 us=853823 pull = DISABLED
Tue May 30 19:22:27 2017 us=853829 auth_user_pass_file = '[UNDEF]'
Tue May 30 19:22:27 2017 us=853836 OpenVPN 2.3.12 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Aug 26 2016
Tue May 30 19:22:27 2017 us=853848 library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.09
Tue May 30 19:22:27 2017 us=853957 NOTE: your local LAN uses the extremely common subnet address 192.168.0.x or 192.168.1.x. Be aware that this might create routing conflicts if you connect to the VPN server from public locations such as internet cafes that use the same subnet.
Tue May 30 19:22:27 2017 us=871320 Diffie-Hellman initialized with 2048 bit key
Tue May 30 19:22:27 2017 us=881102 Control Channel Authentication: using '/etc/openvpn/easy-rsa/keys/ta.key' as a OpenVPN static key file
Tue May 30 19:22:27 2017 us=881147 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:22:27 2017 us=881162 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:22:27 2017 us=881184 TLS-Auth MTU parms [ L:1558 D:1184 EF:66 EB:0 ET:0 EL:3 ]
Tue May 30 19:22:27 2017 us=881205 Socket Buffers: R=[212992->212992] S=[212992->212992]
Tue May 30 19:22:27 2017 us=881326 ROUTE_GATEWAY 192.168.0.1/255.255.255.0 IFACE=enp4s0 HWADDR=80:ee:73:63:54:a6
Tue May 30 19:22:27 2017 us=882327 TUN/TAP device tun0 opened
Tue May 30 19:22:27 2017 us=882387 TUN/TAP TX queue length set to 100
Tue May 30 19:22:27 2017 us=882407 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue May 30 19:22:27 2017 us=882437 /usr/sbin/ifconfig tun0 10.8.0.1 pointopoint 10.8.0.2 mtu 1500
Tue May 30 19:22:27 2017 us=885103 /usr/sbin/route add -net 10.8.0.0 netmask 255.255.255.0 gw 10.8.0.2
Tue May 30 19:22:27 2017 us=885780 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:143 ET:0 EL:3 AF:3/1 ]
Tue May 30 19:22:27 2017 us=886045 GID set to nobody
Tue May 30 19:22:27 2017 us=886066 UID set to nobody
Tue May 30 19:22:27 2017 us=886080 UDPv4 link local (bound): [AF_INET]192.168.0.14:1194
Tue May 30 19:22:27 2017 us=886087 UDPv4 link remote: [undef]
Tue May 30 19:22:27 2017 us=886097 MULTI: multi_init called, r=256 v=256
Tue May 30 19:22:27 2017 us=886120 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0
Tue May 30 19:22:27 2017 us=886143 Initialization Sequence Completed
Tue May 30 19:22:52 2017 us=105110 MULTI: multi_create_instance called
Tue May 30 19:22:52 2017 us=105183 ip_de_ordi_de_pascale:41256 Re-using SSL/TLS context
Tue May 30 19:22:52 2017 us=105214 ip_de_ordi_de_pascale:41256 LZO compression initialized
Tue May 30 19:22:52 2017 us=105281 ip_de_ordi_de_pascale:41256 Control Channel MTU parms [ L:1558 D:1184 EF:66 EB:0 ET:0 EL:3 ]
Tue May 30 19:22:52 2017 us=105292 ip_de_ordi_de_pascale:41256 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:143 ET:0 EL:3 AF:3/1 ]
Tue May 30 19:22:52 2017 us=105313 ip_de_ordi_de_pascale:41256 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-server'
Tue May 30 19:22:52 2017 us=105320 ip_de_ordi_de_pascale:41256 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-client'
Tue May 30 19:22:52 2017 us=105334 ip_de_ordi_de_pascale:41256 Local Options hash (VER=V4): 'a2e63101'
Tue May 30 19:22:52 2017 us=105344 ip_de_ordi_de_pascale:41256 Expected Remote Options hash (VER=V4): '272f1b58'
RTue May 30 19:22:52 2017 us=105375 ip_de_ordi_de_pascale:41256 TLS: Initial packet from [AF_INET]ip_de_ordi_de_pascale:41256, sid=90ff2062 04b02a1c
WRRWWWWRRRRWRWRTue May 30 19:22:52 2017 us=243713 ip_de_ordi_de_pascale:41256 VERIFY OK: depth=1, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=freexuo_vpn, name=EB, emailAddress=eric@famille-bouyoux.fr
Tue May 30 19:22:52 2017 us=243854 ip_de_ordi_de_pascale:41256 VERIFY OK: depth=0, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=ordi_de_pascale, name=EB, emailAddress=eric@famille-bouyoux.fr
WRTue May 30 19:22:52 2017 us=286311 ip_de_ordi_de_pascale:41256 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:22:52 2017 us=286340 ip_de_ordi_de_pascale:41256 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:22:52 2017 us=286349 ip_de_ordi_de_pascale:41256 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:22:52 2017 us=286358 ip_de_ordi_de_pascale:41256 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
WRTue May 30 19:22:52 2017 us=321704 ip_de_ordi_de_pascale:41256 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Tue May 30 19:22:52 2017 us=321735 ip_de_ordi_de_pascale:41256 [ordi_de_pascale] Peer Connection Initiated with [AF_INET]ip_de_ordi_de_pascale:41256
Tue May 30 19:22:52 2017 us=321755 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
Tue May 30 19:22:52 2017 us=321786 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: Learn: 10.8.0.6 -> ordi_de_pascale/ip_de_ordi_de_pascale:41256
Tue May 30 19:22:52 2017 us=321795 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: primary virtual IP for ordi_de_pascale/ip_de_ordi_de_pascale:41256: 10.8.0.6
RTue May 30 19:22:54 2017 us=698333 ordi_de_pascale/ip_de_ordi_de_pascale:41256 PUSH: Received control message: 'PUSH_REQUEST'
Tue May 30 19:22:54 2017 us=698361 ordi_de_pascale/ip_de_ordi_de_pascale:41256 send_push_reply(): safe_cap=940
Tue May 30 19:22:54 2017 us=698386 ordi_de_pascale/ip_de_ordi_de_pascale:41256 SENT CONTROL [ordi_de_pascale]: 'PUSH_REPLY,redirect-gateway def1,route 10.8.0.1 255.255.255.255,route 10.8.0.0 255.255.255.0,route 192.168.0.14 255.255.255.0,dhcp-option DNS 192.168.0.1,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5' (status=1)
WWRRTue May 30 19:22:55 2017 us=743118 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:55 2017 us=940343 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:55 2017 us=978624 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:56 2017 us=216099 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:56 2017 us=423389 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:56 2017 us=693402 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:56 2017 us=910110 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:57 2017 us=640674 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:57 2017 us=884102 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:22:59 2017 us=541153 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:22:59 2017 us=833383 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:00 2017 us=741660 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:01 2017 us=126909 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:02 2017 us=129474 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:03 2017 us=130996 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:23:03 2017 us=336434 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRTue May 30 19:23:03 2017 us=729505 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:04 2017 us=133243 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
WRwRwRTue May 30 19:23:05 2017 us=135004 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:05 2017 us=940781 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRwRwRwRwRwRwRwRwRwRTue May 30 19:23:10 2017 us=936692 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRTue May 30 19:23:11 2017 us=528077 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRwRwRWwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRwRWwRwRwRTue May 30 19:23:26 2017 us=120723 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:23:27 2017 us=112934 ordi_de_pascale/ip_de_ordi_de_pascale:41256 MULTI: bad source address from client [192.168.1.99], packet dropped
client :
Caché:
Tue May 30 19:22:43 2017 OpenVPN 2.3.12 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Aug 26 2016
Tue May 30 19:22:43 2017 library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.09
Tue May 30 19:22:52 2017 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Tue May 30 19:22:52 2017 Control Channel Authentication: tls-auth using INLINE static key file
Tue May 30 19:22:52 2017 UDPv4 link local: [undef]
Tue May 30 19:22:52 2017 UDPv4 link remote: [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:22:52 2017 [freexuo_vpn] Peer Connection Initiated with [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:22:54 2017 TUN/TAP device tun0 opened
Tue May 30 19:22:54 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue May 30 19:22:54 2017 /usr/sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500
route: netmask doesn't match route address
Usage: route [-nNvee] [-FC] [<AF>] List kernel routing tables
route [-v] [-FC] {add|del|flush} ... Modify routing table for AF.
route {-h|--help} [<AF>] Detailed usage syntax for specified AF.
route {-V|--version} Display version/author and exit.
-v, --verbose be verbose
-n, --numeric don't resolve names
-e, --extend display other/more information
-F, --fib display Forwarding Information Base (default)
-C, --cache display routing cache instead of FIB
<AF>=Use -4, -6, '-A <af>' or '--<af>'; default: inet
List of possible address families (which support routing):
inet (DARPA Internet) inet6 (IPv6) ax25 (AMPR AX.25)
netrom (AMPR NET/ROM) ipx (Novell IPX) ddp (Appletalk DDP)
x25 (CCITT X.25)
SIOCADDRT: File exists
Tue May 30 19:22:54 2017 ERROR: Linux route add command failed: external program exited with error status: 7
Tue May 30 19:22:54 2017 Initialization Sequence Completed
Tue May 30 19:22:43 2017 library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.09
Tue May 30 19:22:52 2017 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Tue May 30 19:22:52 2017 Control Channel Authentication: tls-auth using INLINE static key file
Tue May 30 19:22:52 2017 UDPv4 link local: [undef]
Tue May 30 19:22:52 2017 UDPv4 link remote: [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:22:52 2017 [freexuo_vpn] Peer Connection Initiated with [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:22:54 2017 TUN/TAP device tun0 opened
Tue May 30 19:22:54 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue May 30 19:22:54 2017 /usr/sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500
route: netmask doesn't match route address
Usage: route [-nNvee] [-FC] [<AF>] List kernel routing tables
route [-v] [-FC] {add|del|flush} ... Modify routing table for AF.
route {-h|--help} [<AF>] Detailed usage syntax for specified AF.
route {-V|--version} Display version/author and exit.
-v, --verbose be verbose
-n, --numeric don't resolve names
-e, --extend display other/more information
-F, --fib display Forwarding Information Base (default)
-C, --cache display routing cache instead of FIB
<AF>=Use -4, -6, '-A <af>' or '--<af>'; default: inet
List of possible address families (which support routing):
inet (DARPA Internet) inet6 (IPv6) ax25 (AMPR AX.25)
netrom (AMPR NET/ROM) ipx (Novell IPX) ddp (Appletalk DDP)
x25 (CCITT X.25)
SIOCADDRT: File exists
Tue May 30 19:22:54 2017 ERROR: Linux route add command failed: external program exited with error status: 7
Tue May 30 19:22:54 2017 Initialization Sequence Completed
Config2 : source = Vouf
serveur :
adresse IP locale : 192.168.0.14
config serveur :
Caché:
# adresse locale du serveur
local 192.168.0.14
# type d'interface
dev tun
# protocole de communication
proto udp
# numéro du port utilisé
port 1194
# emplacement du master CA
ca /etc/openvpn/easy-rsa/keys/ca.crt
# emplacement du certificat du serveur
cert /etc/openvpn/easy-rsa/keys/freexuo_vpn.crt
# emplacement de la clé du serveur
key /etc/openvpn/easy-rsa/keys/freexuo_vpn.key
# emplacement du fichier Diffie-Hellman
dh /etc/openvpn/easy-rsa/keys/dh2048.pem
# quelle sera l'adresse du réseau virtuel créé par le VPN
# l'adresse du serveur VPN
server 10.8.0.0 255.255.255.0
# serveur et point de sortie distant
# ifconfig 10.8.0.1 10.8.0.2
push "redirect-gateway def1"
# push "route 10.8.0.1 255.255.255.255" # route vers le serveur VPN
# push "route 10.8.0.0 255.255.255.0" # route vers le sous-réseau VPN
# push "route 192.168.0.14 255.255.255.0" #sous-réseau local - adaptez l'adresse IP locale de votre serveur
# push "dhcp-option DNS 192.168.0.1" # votre serveur DNS primaire (votre routeur, souvent)
push "dhcp-option DNS 10.8.0.1" # votre serveur DNS primaire (votre routeur, souvent)
# push "dhcp-option DNS 8.8.8.8" # votre serveur DNS primaire (votre routeur, souvent)
#push "route 192.168.0.0 255.255.255.0"
#push "redirect-gateway def1 bypass-dhcp"
client-to-client
duplicate-cn
tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0
#
keepalive 10 120
#type d'encryptage des données
cipher AES-128-CBC
#activation de la compression
comp-lzo
#nombre maximum de clients autorisés
max-clients 2
#pas d'utilisateur et groupe particuliers pour l'utilisation du VPN
user nobody
group nobody
#pour rendre la connexion persistante
persist-key
persist-tun
#fichier de log
status /var/log/openvpn-status.log 20
log /var/log/openvpn.log
# niveau de verbosité
verb 5
local 192.168.0.14
# type d'interface
dev tun
# protocole de communication
proto udp
# numéro du port utilisé
port 1194
# emplacement du master CA
ca /etc/openvpn/easy-rsa/keys/ca.crt
# emplacement du certificat du serveur
cert /etc/openvpn/easy-rsa/keys/freexuo_vpn.crt
# emplacement de la clé du serveur
key /etc/openvpn/easy-rsa/keys/freexuo_vpn.key
# emplacement du fichier Diffie-Hellman
dh /etc/openvpn/easy-rsa/keys/dh2048.pem
# quelle sera l'adresse du réseau virtuel créé par le VPN
# l'adresse du serveur VPN
server 10.8.0.0 255.255.255.0
# serveur et point de sortie distant
# ifconfig 10.8.0.1 10.8.0.2
push "redirect-gateway def1"
# push "route 10.8.0.1 255.255.255.255" # route vers le serveur VPN
# push "route 10.8.0.0 255.255.255.0" # route vers le sous-réseau VPN
# push "route 192.168.0.14 255.255.255.0" #sous-réseau local - adaptez l'adresse IP locale de votre serveur
# push "dhcp-option DNS 192.168.0.1" # votre serveur DNS primaire (votre routeur, souvent)
push "dhcp-option DNS 10.8.0.1" # votre serveur DNS primaire (votre routeur, souvent)
# push "dhcp-option DNS 8.8.8.8" # votre serveur DNS primaire (votre routeur, souvent)
#push "route 192.168.0.0 255.255.255.0"
#push "redirect-gateway def1 bypass-dhcp"
client-to-client
duplicate-cn
tls-auth /etc/openvpn/easy-rsa/keys/ta.key 0
#
keepalive 10 120
#type d'encryptage des données
cipher AES-128-CBC
#activation de la compression
comp-lzo
#nombre maximum de clients autorisés
max-clients 2
#pas d'utilisateur et groupe particuliers pour l'utilisation du VPN
user nobody
group nobody
#pour rendre la connexion persistante
persist-key
persist-tun
#fichier de log
status /var/log/openvpn-status.log 20
log /var/log/openvpn.log
# niveau de verbosité
verb 5
Config client : idem que la précédente.
Résultats pour la config 2 :
serveur :
Caché:
Tue May 30 19:13:12 2017 us=827035 MULTI: multi_create_instance called
Tue May 30 19:13:12 2017 us=843164 ip_de_ordi_de_pascale:44585 Re-using SSL/TLS context
Tue May 30 19:13:12 2017 us=843219 ip_de_ordi_de_pascale:44585 LZO compression initialized
Tue May 30 19:13:12 2017 us=843311 ip_de_ordi_de_pascale:44585 Control Channel MTU parms [ L:1558 D:1184 EF:66 EB:0 ET:0 EL:3 ]
Tue May 30 19:13:12 2017 us=843322 ip_de_ordi_de_pascale:44585 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:143 ET:0 EL:3 AF:3/1 ]
Tue May 30 19:13:12 2017 us=861569 ip_de_ordi_de_pascale:44585 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-server'
Tue May 30 19:13:12 2017 us=861637 ip_de_ordi_de_pascale:44585 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-client'
Tue May 30 19:13:12 2017 us=861665 ip_de_ordi_de_pascale:44585 Local Options hash (VER=V4): 'a2e63101'
Tue May 30 19:13:12 2017 us=861683 ip_de_ordi_de_pascale:44585 Expected Remote Options hash (VER=V4): '272f1b58'
RTue May 30 19:13:12 2017 us=861772 ip_de_ordi_de_pascale:44585 TLS: Initial packet from [AF_INET]ip_de_ordi_de_pascale:44585, sid=974e71f7 2790029a
WRRWWWWRRRRWRWRTue May 30 19:13:13 2017 us=1557 ip_de_ordi_de_pascale:44585 VERIFY OK: depth=1, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=freexuo_vpn, name=EB, emailAddress=eric@famille-bouyoux.fr
Tue May 30 19:13:13 2017 us=1715 ip_de_ordi_de_pascale:44585 VERIFY OK: depth=0, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=ordi_de_pascale, name=EB, emailAddress=eric@famille-bouyoux.fr
WRTue May 30 19:13:13 2017 us=43221 ip_de_ordi_de_pascale:44585 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:13:13 2017 us=43241 ip_de_ordi_de_pascale:44585 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:13:13 2017 us=43251 ip_de_ordi_de_pascale:44585 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:13:13 2017 us=43260 ip_de_ordi_de_pascale:44585 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
WRTue May 30 19:13:13 2017 us=77937 ip_de_ordi_de_pascale:44585 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Tue May 30 19:13:13 2017 us=77965 ip_de_ordi_de_pascale:44585 [ordi_de_pascale] Peer Connection Initiated with [AF_INET]ip_de_ordi_de_pascale:44585
Tue May 30 19:13:13 2017 us=77985 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
Tue May 30 19:13:13 2017 us=78016 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: Learn: 10.8.0.6 -> ordi_de_pascale/ip_de_ordi_de_pascale:44585
Tue May 30 19:13:13 2017 us=78025 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: primary virtual IP for ordi_de_pascale/ip_de_ordi_de_pascale:44585: 10.8.0.6
RTue May 30 19:13:15 2017 us=123558 ordi_de_pascale/ip_de_ordi_de_pascale:44585 PUSH: Received control message: 'PUSH_REQUEST'
Tue May 30 19:13:15 2017 us=123598 ordi_de_pascale/ip_de_ordi_de_pascale:44585 send_push_reply(): safe_cap=940
Tue May 30 19:13:15 2017 us=123620 ordi_de_pascale/ip_de_ordi_de_pascale:44585 SENT CONTROL [ordi_de_pascale]: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.8.0.1,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5' (status=1)
WWRRwRTue May 30 19:13:16 2017 us=405738 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:16 2017 us=801827 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:17 2017 us=192795 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:17 2017 us=980831 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:19 2017 us=272333 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:19 2017 us=559848 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:20 2017 us=284627 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:20 2017 us=936366 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:21 2017 us=276347 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:21 2017 us=938147 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:22 2017 us=278135 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:22 2017 us=712943 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:22 2017 us=940396 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:23 2017 us=280390 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:23 2017 us=942191 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:24 2017 us=944446 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
WRwRTue May 30 19:13:26 2017 us=404977 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRwRwRwRwRTue May 30 19:13:29 2017 us=17057 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
Tue May 30 19:13:12 2017 us=843164 ip_de_ordi_de_pascale:44585 Re-using SSL/TLS context
Tue May 30 19:13:12 2017 us=843219 ip_de_ordi_de_pascale:44585 LZO compression initialized
Tue May 30 19:13:12 2017 us=843311 ip_de_ordi_de_pascale:44585 Control Channel MTU parms [ L:1558 D:1184 EF:66 EB:0 ET:0 EL:3 ]
Tue May 30 19:13:12 2017 us=843322 ip_de_ordi_de_pascale:44585 Data Channel MTU parms [ L:1558 D:1450 EF:58 EB:143 ET:0 EL:3 AF:3/1 ]
Tue May 30 19:13:12 2017 us=861569 ip_de_ordi_de_pascale:44585 Local Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 0,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-server'
Tue May 30 19:13:12 2017 us=861637 ip_de_ordi_de_pascale:44585 Expected Remote Options String: 'V4,dev-type tun,link-mtu 1558,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-128-CBC,auth SHA1,keysize 128,tls-auth,key-method 2,tls-client'
Tue May 30 19:13:12 2017 us=861665 ip_de_ordi_de_pascale:44585 Local Options hash (VER=V4): 'a2e63101'
Tue May 30 19:13:12 2017 us=861683 ip_de_ordi_de_pascale:44585 Expected Remote Options hash (VER=V4): '272f1b58'
RTue May 30 19:13:12 2017 us=861772 ip_de_ordi_de_pascale:44585 TLS: Initial packet from [AF_INET]ip_de_ordi_de_pascale:44585, sid=974e71f7 2790029a
WRRWWWWRRRRWRWRTue May 30 19:13:13 2017 us=1557 ip_de_ordi_de_pascale:44585 VERIFY OK: depth=1, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=freexuo_vpn, name=EB, emailAddress=eric@famille-bouyoux.fr
Tue May 30 19:13:13 2017 us=1715 ip_de_ordi_de_pascale:44585 VERIFY OK: depth=0, C=FR, ST=PACA, L=Bouc-Bel-Air, O=Famille-Bouyoux, OU=Famille-Bouyoux, CN=ordi_de_pascale, name=EB, emailAddress=eric@famille-bouyoux.fr
WRTue May 30 19:13:13 2017 us=43221 ip_de_ordi_de_pascale:44585 Data Channel Encrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:13:13 2017 us=43241 ip_de_ordi_de_pascale:44585 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Tue May 30 19:13:13 2017 us=43251 ip_de_ordi_de_pascale:44585 Data Channel Decrypt: Cipher 'AES-128-CBC' initialized with 128 bit key
Tue May 30 19:13:13 2017 us=43260 ip_de_ordi_de_pascale:44585 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
WRTue May 30 19:13:13 2017 us=77937 ip_de_ordi_de_pascale:44585 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Tue May 30 19:13:13 2017 us=77965 ip_de_ordi_de_pascale:44585 [ordi_de_pascale] Peer Connection Initiated with [AF_INET]ip_de_ordi_de_pascale:44585
Tue May 30 19:13:13 2017 us=77985 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI_sva: pool returned IPv4=10.8.0.6, IPv6=(Not enabled)
Tue May 30 19:13:13 2017 us=78016 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: Learn: 10.8.0.6 -> ordi_de_pascale/ip_de_ordi_de_pascale:44585
Tue May 30 19:13:13 2017 us=78025 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: primary virtual IP for ordi_de_pascale/ip_de_ordi_de_pascale:44585: 10.8.0.6
RTue May 30 19:13:15 2017 us=123558 ordi_de_pascale/ip_de_ordi_de_pascale:44585 PUSH: Received control message: 'PUSH_REQUEST'
Tue May 30 19:13:15 2017 us=123598 ordi_de_pascale/ip_de_ordi_de_pascale:44585 send_push_reply(): safe_cap=940
Tue May 30 19:13:15 2017 us=123620 ordi_de_pascale/ip_de_ordi_de_pascale:44585 SENT CONTROL [ordi_de_pascale]: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.8.0.1,route 10.8.0.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 10.8.0.6 10.8.0.5' (status=1)
WWRRwRTue May 30 19:13:16 2017 us=405738 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:16 2017 us=801827 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:17 2017 us=192795 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:17 2017 us=980831 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:19 2017 us=272333 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:19 2017 us=559848 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:20 2017 us=284627 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:20 2017 us=936366 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:21 2017 us=276347 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:21 2017 us=938147 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:22 2017 us=278135 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:22 2017 us=712943 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:22 2017 us=940396 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RTue May 30 19:13:23 2017 us=280390 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:23 2017 us=942191 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRTue May 30 19:13:24 2017 us=944446 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
WRwRTue May 30 19:13:26 2017 us=404977 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
RwRwRwRwRwRwRwRTue May 30 19:13:29 2017 us=17057 ordi_de_pascale/ip_de_ordi_de_pascale:44585 MULTI: bad source address from client [192.168.1.99], packet dropped
client :
Caché:
Tue May 30 19:12:57 2017 library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.09
Tue May 30 19:13:12 2017 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Tue May 30 19:13:12 2017 Control Channel Authentication: tls-auth using INLINE static key file
Tue May 30 19:13:12 2017 UDPv4 link local: [undef]
Tue May 30 19:13:12 2017 UDPv4 link remote: [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:13:13 2017 [freexuo_vpn] Peer Connection Initiated with [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:13:15 2017 TUN/TAP device tun0 opened
Tue May 30 19:13:15 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue May 30 19:13:15 2017 /usr/sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500
Tue May 30 19:13:15 2017 Initialization Sequence Completed
Tue May 30 19:13:12 2017 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Tue May 30 19:13:12 2017 Control Channel Authentication: tls-auth using INLINE static key file
Tue May 30 19:13:12 2017 UDPv4 link local: [undef]
Tue May 30 19:13:12 2017 UDPv4 link remote: [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:13:13 2017 [freexuo_vpn] Peer Connection Initiated with [AF_INET]ip_de_xuo.fr:1194
Tue May 30 19:13:15 2017 TUN/TAP device tun0 opened
Tue May 30 19:13:15 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue May 30 19:13:15 2017 /usr/sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500
Tue May 30 19:13:15 2017 Initialization Sequence Completed
Pouvez-vous m'aider à mettre au point cette connexion ?
Merci.
Xuo.
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
Mon test avait été réalisé avec un serveur openvpn debian. Actuellement, vu que j'ai tout porté sur mon NAS, c'est beaucoup plus simple. Je pense qu'il manque pas grand chose vu l'aspect des logs. Je vais travailler le sujet ce weekend de mon côté avec un POC serveur Mageia + client Mageia. Je te tiens au jus..
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
xuo Membre non connecté
-

- Voir le profil du membre xuo
- Inscrit le : 23/10/2011
- Groupes :
Merci de m'aider. Hier soir, je n'ai pas eu le temps de me remettre dessus. J'ai trouvé un autre document. J'espère pouvoir travailler dessus ce soir (si la mise à jour de Teampass m'en laisse le temps). J'ai "l'impression" que j'ai des iptables qui ne sont pas configurées correctement.
Xuo.
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
J'ai réussi via deux machines virtuelles sous mageia 6 à monter un poc avec un serveur et un client openvpn. Je vais démarrer la documentation sur le wiki de mlo à cet emplacement .
J'arrive à faire fonctionner l'ensemble, mais j'aurai besoin de toi pour valider la procédure et la consolider. C'est une opération lourde qui nécessite de comprendre ce que l'on fait.
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
xuo Membre non connecté
-

- Voir le profil du membre xuo
- Inscrit le : 23/10/2011
- Groupes :
Désolé, je n'avais pas vu que vous aviez répondu.
Il y a des choses que je ne comprends pas.
Si je lance un route -n depuis le serveur openvpn :
/usr/share 153 # route -n
Table de routage IP du noyau
Destination Passerelle Genmask Indic Metric Ref Use Iface
0.0.0.0 192.168.0.1 0.0.0.0 UG 5 0 0 enp4s0
10.8.0.0 10.8.0.2 255.255.255.0 UG 0 0 0 tun0
10.8.0.2 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
169.254.0.0 0.0.0.0 255.255.0.0 U 5 0 0 enp4s0
192.168.0.0 0.0.0.0 255.255.255.0 U 5 0 0 enp4s0
239.0.0.0 0.0.0.0 255.0.0.0 U 5 0 0 enp4s0
Je ne vois pas ce que sont ces 2 adresses 169.254.0.0 et 239.0.0.0
De plus, j'ai toujours sur le fichier de log du serveur :
RTue Jun 6 20:45:34 2017 us=230593 ordi_de_pascale/<add IP de la bBox du client>:53477 MULTI: bad source address from client [192.168.1.99], packet dropped
Par contre, côté client, le log est propre :
/root 76 # cat /var/log/openvpn.log
Tue Jun 6 20:43:44 2017 OpenVPN 2.3.12 x86_64-mageia-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Aug 26 2016
Tue Jun 6 20:43:44 2017 library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.09
Tue Jun 6 20:43:51 2017 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Tue Jun 6 20:43:51 2017 Control Channel Authentication: tls-auth using INLINE static key file
Tue Jun 6 20:43:51 2017 UDPv4 link local: [undef]
Tue Jun 6 20:43:51 2017 UDPv4 link remote: [AF_INET]<Add IP de la LiveBox du serveur>:1194
Tue Jun 6 20:43:52 2017 [freexuo_vpn] Peer Connection Initiated with [AF_INET]<Add IP de la LiveBox du serveur>:1194
Tue Jun 6 20:43:54 2017 TUN/TAP device tun0 opened
Tue Jun 6 20:43:54 2017 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue Jun 6 20:43:54 2017 /usr/sbin/ifconfig tun0 10.8.0.6 pointopoint 10.8.0.5 mtu 1500
Tue Jun 6 20:43:54 2017 Initialization Sequence Completed
Mais sur l'icône réseau du client :
adresse IP : 10.8.0.6
Passerelle : 10.8.0.5
DNS : 192.168.1.254
J'ai l'impression que le DNS n'est pas bon.
Xuo.
Édité par xuo Le 06/06/2017 à 20h53
xuo Membre non connecté
-

- Voir le profil du membre xuo
- Inscrit le : 23/10/2011
- Groupes :
le route -n depuis le client :
/etc 85 # route -n
Table de routage IP du noyau
Destination Passerelle Genmask Indic Metric Ref Use Iface
0.0.0.0 10.8.0.5 128.0.0.0 UG 0 0 0 tun0
0.0.0.0 192.168.1.254 0.0.0.0 UG 35 0 0 wlp3s0
<Add IP de la liveBox du serveur> 192.168.1.254 255.255.255.255 UGH 0 0 0 wlp3s0
10.8.0.0 10.8.0.5 255.255.255.0 UG 0 0 0 tun0
10.8.0.5 0.0.0.0 255.255.255.255 UH 0 0 0 tun0
128.0.0.0 10.8.0.5 128.0.0.0 UG 0 0 0 tun0
192.168.1.0 0.0.0.0 255.255.255.0 U 35 0 0 wlp3s0
Xuo.
vouf Membre non connecté
-

- Voir le profil du membre vouf
- Inscrit le : 16/08/2008
- Groupes :
Pour le dns, je ne sais pas si tu l'as vu au niveau du wiki, je les ai forcé dans la conf du serveur.
Code TEXT :
... push "redirect-gateway def1 bypass-dhcp" # Permet au serveur de se comporter comme une passerelle. #push "dhcp-option DNS 10.8.0.1" # votre serveur DNS primaire (votre routeur, souvent) push "dhcp-option DNS 208.67.222.222" # votre serveur DNS primaire OpenDNS push "dhcp-option DNS 208.67.220.220" # votre serveur DNS primaire OpenDNS ....
Pour tester le dns, il faut utiliser nslookup ou dig.
Pour 239.0.0.0, tu n'aurais pas un virtualbox qui aurait modifier ta conf réseau ? Peux tu toujours supprimer cette adresse via le centre de contrôle mageia. Sinon, peux tu me remontrer ta conf de ton serveur openvpn.
Mageia 9 64 bits Plasma - Asus Prime Z690-P D4 -Intel Core i5 12600 K- 32 Go Kingston Fury Renegade DDR4-3600 Mhz- Gigabyte Nvidia RTX 3060 - Go-M2 Samsung Evo 970 1Tb-SSD 512 Gb Samsung Evo 960 -SSD 512 Gb Crucial M5
xuo Membre non connecté
-

- Voir le profil du membre xuo
- Inscrit le : 23/10/2011
- Groupes :
Oui j'ai bien mis la même chose dans mon serveur.conf.
Je le mets en ligne ce soir. Et je regarde si je peux trouver quelque chose avec le nslookup.
Xuo.
Répondre
Vous n'êtes pas autorisé à écrire dans cette catégorie